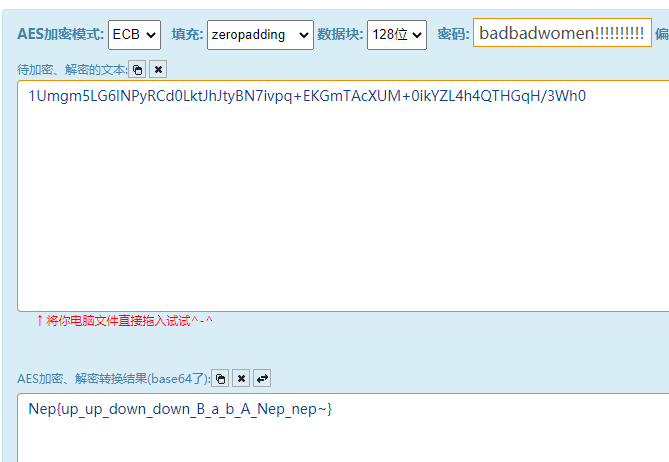
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
| private static void Main(string[] args)
{
AesClass class2 = new AesClass();
string key = "";
string strB = "1Umgm5LG6lNPyRCd0LktJhJtyBN7ivpq+EKGmTAcXUM+0ikYZL4h4QTHGqH/3Wh0";
byte[] buffer = new byte[] {
0x51, 0x52, 0x57, 0x51, 0x52, 0x57, 0x44, 0x5c, 0x5e, 0x56, 0x5d, 0x12, 0x12, 0x12, 0x12, 0x12,
0x12, 0x12, 0x12, 0x12, 0x12, 0x12, 0x12, 0x12, 0x12, 0x12, 0x12, 0x12, 0x12, 0x12, 0x12, 0x12
};
Console.WriteLine("Welcome to nepnep csharp test! plz input the magical code:");
string str = Console.ReadLine();
if (str.Length != 0x25)
{
Console.WriteLine("Nope!");
Console.ReadKey();
}
else if ((str.Substring(0, 4) != "Nep{") || (str[0x24] != '}'))
{
Console.WriteLine("Nope!");
Console.ReadKey();
}
else
{
for (int i = 0; i < 0x20; i++)
{
key = key + Convert.ToChar((int) (buffer[i] ^ 0x33)).ToString();
}
if (string.Compare(class2.AesEncrypt(str, key), strB) == 0)
{
Console.WriteLine("wow, you pass it!");
Console.ReadKey();
}
else
{
Console.WriteLine("Nope!");
Console.ReadKey();
}
}
}
|